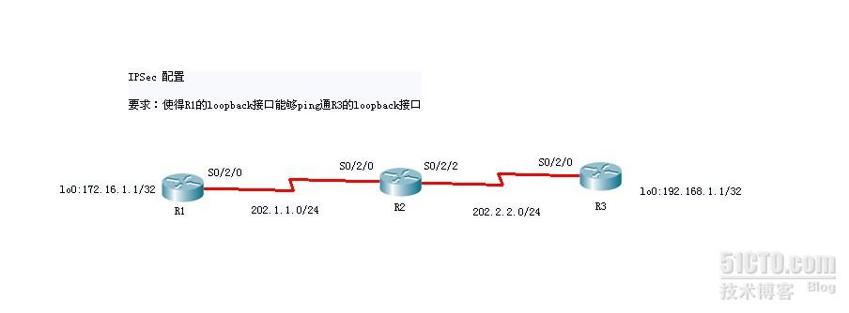
H3C IPSec配置实例
发布时间:2019-09-07 08:10:53编辑:auto阅读(2751)
配置步骤:
一、.使得R1与R3之间(公网之间)能够通信
[R1]ip route-static
[R3]ip route-static
二、IPSEC配置
R1配置:
1.配置感兴趣的数据流
[R1]acl num 3000
[R1-acl-adv-3000]rule permit ip source 192.168.1.1
2.IKE策略配置
[R1]ike proposal 10 //创建IKE提议,并进入IKE视图
[R1-ike-proposal-10]encryption-algorithm 3des-cbc //IKE提议使用的加密算法
[R1-ike-proposal-10]authentication-method pre-share //IKE提议使用的密钥处理方式
[R1-ike-proposal-10]authentication-algorithm md5 //IKE提议使用的验证算法
[R1-ike-proposal-10]dh group2 //IKE提议使用的DH交换组
[R1-ike-proposal-10]sa duration 86400 //ISAKMP SA生存周期
[R1-ike-proposal-10]
3.配置IKE对等体及密钥
[R1]ike peer R3 //创建IKE对等体,并进入IKE对等体视图
[R1-ike-peer-r3]exchange-mode main //IKE对等体的协商模式
[R1-ike-peer-r3]pre-shared-key h
[R1-ike-peer-r3]local-address
[R1-ike-peer-r3]remote-address
[R1-ike-peer-r3]remote-name R3 //对端安全网关名称
[R1]ike local-name R1 //本端安全网关名称
[R1]
4. IPSEC安全提议配置
[R1]ipsec proposal r1 //创建IPSEC安全提议
[R1-ipsec-proposal-r1]transform esp //安全协议
[R1-ipsec-proposal-r1]esp encryption-algorithm 3des //ESP协议采用加密算法
[R1-ipsec-proposal-r1]esp authentication-algorithm md5 //ESP协议采用验证算法
[R1-ipsec-proposal-r1]encapsulation-mode tunnel //ESP协议采用工作模式
[R1-ipsec-proposal-r1]
5.配置IKE协商的安全策略
[R1]ipsec policy 1 10 isakmp //创建一条安全策略
[R1-ipsec-policy-isakmp-1-10]security acl 3000 //配置安全c策略所引用的ACL
[R1-ipsec-policy-isakmp-1-10]proposal r1 //配安全策略所引用的安全提议
[R1-ipsec-policy-isakmp-1-10]ike-peer r3 //引用的IKE对等体
[R1-ipsec-policy-isakmp-1-10]pfs dh-group5 //DH组
[R1-ipsec-policy-isakmp-1-10]sa duration time-based 86400 //ipsec SA生存周期
[R1-ipsec-policy-isakmp-1-10]q
6.在接口上应用安全策略
[R1]int s0/2/0
[R1-Serial0/2/0]ipsec policy 1 //在接口上应用安全策略
[R1]
R3的配置
[R3]ip route-static
[R3]acl number 3000
[R3-acl-adv-3000]rule pe
[R3-acl-adv-3000]rule permit ip source 192.168.2.1
[R3-acl-adv-3000]q
[R3]ike proposal 10
[R3-ike-proposal-10]encryption-algorithm 3des-cbc
[R3-ike-proposal-10]authentication-method pre-share
[R3-ike-proposal-10]authentication-algorithm md5
[R3-ike-proposal-10]dh group2
[R3-ike-proposal-10]sa duration 86400
[R3-ike-proposal-10]q
[R3]ike peer R1
[R3-ike-peer-r1]exchange-mode main
[R3-ike-peer-r1]pre-shared-key h
[R3-ike-peer-r1]local-
[R3-ike-peer-r1]remote-address
[R3-ike-peer-r1]remote-name R1
[R3-ike-peer-r1]Q
[R3]ipsec proposal r3
[R3-ipsec-proposal-r3]transform esp
[R3-ipsec-proposal-r3]esp encryption-algorithm 3des
[R3-ipsec-proposal-r3]esp authentication-algorithm md5
[R3-ipsec-proposal-r3]encapsulation-mode tunnel
[R3-ipsec-proposal-r3]q
[R3]ipsec policy 1 10 isakmp
[R3-ipsec-policy-isakmp-1-10]security acl 3000
[R3-ipsec-policy-isakmp-1-10]proposal r3
[R3-ipsec-policy-isakmp-1-10]ike-peer R1
[R3-ipsec-policy-isakmp-1-10]sa duration time-based 86400
[R3-ipsec-policy-isakmp-1-10]q
[R3]int s0/2/0
[R3-Serial0/2/0]ipsec policy 1
[R3-Serial0/2/0]q
三、测试实验结果
[R1]ping -a 192.168.1.1 192.168.2.1
Reply from 192.168.2.1: bytes=56 Sequence=1 ttl=255 time=5 ms
Reply from 192.168.2.1: bytes=56 Sequence=2 ttl=255 time=20 ms
Request time out
Reply from 192.168.2.1: bytes=56 Sequence=4 ttl=255 time=26 ms
Request time out
--- 192.168.2.1 ping statistics ---
5 packet(s) transmitted
3 packet(s) received
40.00% packet loss
round-trip min/avg/max =
[R1]
此时两个内网之间能够正常通信。实验完成
调试命令:
1.显示IKE对等体配置参数
[R1]dis ike peer
---------------------------
IKE Peer: r3
exchange mode: main on phase 1
pre-shared-key cipher nw1kqzgZJnA=
peer id type: ip
peer ip address:
local ip address:
peer name: R3
nat traversal: disable
dpd:
---------------------------
[R1]
2.显示当前ISAKMP SA的信息
[R1]dis ike sa
total phase-1 SAs: 1
connection-id peer flag phase doi
----------------------------------------------------------
3
2
flag meaning
RD--
[R1]
3.显示每个IKE提议的配置参数
[R1]dis ike sa
total phase-1 SAs: 1
connection-id peer flag phase doi
----------------------------------------------------------
3
2
flag meaning
RD--
[R1]dis ike pro
[R1]dis ike proposal
priority authentication authentication encryption Diffie-Hellman duration
method algorithm algorithm group (seconds)
---------------------------------------------------------------------------
10 PRE_SHARED MD5 3DES_CBC MODP_1024 86400
default PRE_SHARED SHA DES_CBC MODP_768 86400
[R1]
4.显示IPsec安全策略信息
[R1]dis ipsec policy
===========================================
IPsec Policy Group: "1"
Using interface: {Serial0/2/0}
===========================================
-----------------------------
IPsec policy name: "1"
sequence number: 10
mode: isakmp
-----------------------------
security data flow : 3000
selector mode: standard
ike-peer name: r3
perfect forward secrecy: DH group 5
proposal name: r1
IPsec sa local duration(time based): 86400 seconds
IPsec sa local duration(traffic based): 1843200 kilobytes
[R1]
5.显示IPSEC安全提议信息
[R1]dis ipsec proposal
IPsec proposal name: r1
encapsulation mode: tunnel
transform: esp-new
ESP protocol: authentication md5-hmac-96, encryption 3des
[R1]
6.显示IPSEC SA的信息
[R1]dis ipsec sa
===============================
Interface: Serial0/2/0
path MTU: 1500
===============================
-----------------------------
IPsec policy name: "1"
sequence number: 10
mode: isakmp
-----------------------------
connection id: 3
encapsulation mode: tunnel
perfect forward secrecy: DH group 5
tunnel:
local address:
remote address:
Flow :
sour addr: 192.168.1.1/255.255.255.255 port: 0 protocol: IP
dest addr: 192.168.2.1/255.255.255.255 port: 0 protocol: IP
[inbound ESP SAs]
spi: 2476921505 (0x
proposal: ESP-ENCRYPT-3DES ESP-AUTH-MD5
sa remaining key duration (bytes/sec): 1887435624/84789
max received sequence-number: 14
udp encapsulation used for nat traversal: N
[outbound ESP SAs]
spi: 1974141924 (0x75ab03e4)
proposal: ESP-ENCRYPT-3DES ESP-AUTH-MD5
sa remaining key duration (bytes/sec): 1887435624/84789
max sent sequence-number: 15
udp encapsulation used for nat traversal: N
[R1]
7.显示IPSEC处理的报文信息
[R1]dis ipsec statistics
the security packet statistics:
input/output security packets: 14/14
input/output security bytes: 1176/1176
input/output dropped security packets: 0/1
dropped security packet detail:
not enough memory: 0
can't find SA: 1
queue is full: 0
authentication has failed: 0
wrong length: 0
replay packet: 0
packet too long: 0
wrong SA: 0
[R1]
上一篇: H3C FTP 升级路由器
下一篇: javascript加CSS3做不一样的
- openvpn linux客户端使用
51931
- H3C基本命令大全
51705
- openvpn windows客户端使用
42021
- H3C IRF原理及 配置
38860
- Python exit()函数
33346
- openvpn mac客户端使用
30315
- python全系列官方中文文档
28958
- python 获取网卡实时流量
23971
- 1.常用turtle功能函数
23885
- python 获取Linux和Windows硬件信息
22252
- Ubuntu本地部署dots.ocr
383°
- Python搭建一个RAG系统(分片/检索/召回/重排序/生成)
2590°
- Browser-use:智能浏览器自动化(Web-Agent)
3261°
- 使用 LangChain 实现本地 Agent
2714°
- 使用 LangChain 构建本地 RAG 应用
2702°
- 使用LLaMA-Factory微调大模型的function calling能力
3436°
- 复现一个简单Agent系统
2657°
- LLaMA Factory-Lora微调实现声控语音多轮问答对话-1
3499°
- LLaMA Factory微调后的模型合并导出和部署-4
5771°
- LLaMA Factory微调模型的各种参数怎么设置-3
5545°
- 姓名:Run
- 职业:谜
- 邮箱:383697894@qq.com
- 定位:上海 · 松江