H3C-×××的配置
发布时间:2019-08-17 08:51:07编辑:auto阅读(1975)
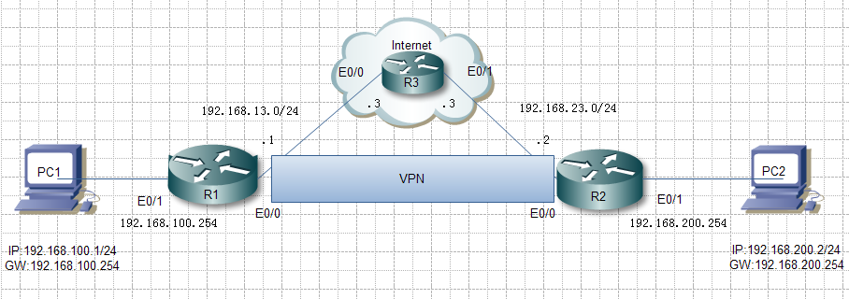
- 配置IP地址
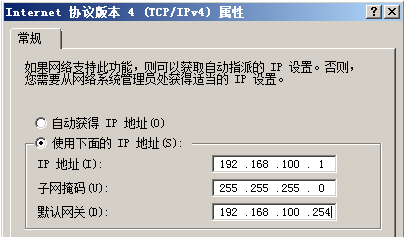
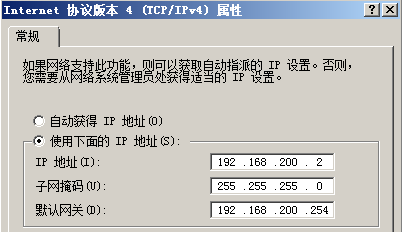
<R1>system-view[R1]interface e0/1[R1-Ethernet0/1]ip address 192.168.100.254 255.255.255.0[R1]interface e0/0[R1-Ethernet0/0]ip address 192.168.13.1 255.255.255.0<R2>system-view[R2]interface e0/1[R2-Ethernet0/1]ip address 192.168.200.254 255.255.255.0[R2]interface e0/0[R2-Ethernet0/0]ip address 192.168.23.2 255.255.255.0<R3>system-view[R3]interface e0/0[R3-Ethernet0/0]ip address 192.168.13.3 255.255.255.0[R3]interface e0/1[R3-Ethernet0/1]ip address 192.168.23.3 255.255.255.0PC1的设置PC2的设置
-
配置手工方式的Tunnel[R1]acl 3000[R1-acl-3000]rule permit ip source 192.168.100.1 0.0.0.255 destination 192.168.200.2 0.0.0.255[R1-acl-3000]rule deny ip source any destination any[R1-acl-3000]quit//创建访问规则[R1]ipsec proposal trans1[R1-ipsec-proposal-trans1]encapsulation-mode tunnel[R1-ipsec-proposal-trans1]transform esp-new[R1-ipsec-proposal-trans1]esp-new authentication md5-hmac-96[R1-ipsec-proposal-trans1]esp-new encryption-algorithm des[R1-ipsec-proposal-trans1]quit//创建提议,以及对提议的加密、认证方式[R1]ipsec policy p1 100 manual[R1-ipsec-policy-p1-100]security acl 3000[R1-ipsec-policy-p1-100]proposal trans1[R1-ipsec-policy-p1-100]tunnel local 192.168.13.1[R1-ipsec-policy-p1-100]tunnel remote 192.168.23.2[R1-ipsec-policy-p1-100]sa inbound esp spi 123456[R1-ipsec-policy-p1-100]sa inbound esp string-key asdf[R1-ipsec-policy-p1-100]sa outbound esp spi 654321[R1-ipsec-policy-p1-100]sa outbound esp string-key fdsa[R1-ipsec-policy-pl -100]quit//创建策略,包含上述提议,该策略将应用于Tunnel中,需要注意的是Tunnel两端的路由器策略配置,R1中的tunnel local地址是R2的tunnel remote, inbound是R2的outbound。[R1]interface e0/0[R1-Ethernet0/0]ipsec policy p1//在出口上应用策略[R2]acl 3001[R2-acl-3001]rule permit ip source 192.168.200.2 0.0.0.255 destination 192.168.100.1 0.0.0.255[R2-acl-3001]rule deny ip source any destination any[R2-acl-3001]quit//创建访问规则[R2]ipsec proposal trans2[R2-ipsec-proposal-trans2]encapsulation-mode tunnel[R2-ipsec-proposal-trans2]transform esp-new[R2-ipsec-proposal-trans2]esp-new authentication md5-hmac-96[R2-ipsec-proposal-trans2]esp-new encryption-algorithm des[R2-ipsec-proposal-trans2]quit//创建提议,以及对提议的加密、认证方式[R2]ipsec policy p2 200 manual[R2-ipsec-policy-p2-200]security acl 3001[R2-ipsec-policy-p2-200]proposal trans2[R2-ipsec-policy-p2-200]tunnel local 192.168.23.2[R2-ipsec-policy-p2-200]tunnel remote 192.168.13.1[R2-ipsec-policy-p2-200]sa inbound esp spi 654321[R2-ipsec-policy-p2-200]sa inbound esp string-key fdsa[R2-ipsec-policy-p2-200]sa outbound esp spi 123456[R2-ipsec-policy-p2-200]sa outbound esp string-key asdf[R2-ipsec-policy-p2-200]quit[R2]interface e0/0[R2-Ethernet0/0]ipsec policy p2
-
在Tunnel两端的路由器上各添加一条默认路由,是内网地址能够和外部连接。ip route-static 0.0.0.0 0.0.0.0 192.168.13.3 preference 60 //R1上的默认路由ip route-static 0.0.0.0 0.0.0.0 192.168.23.3 preference 60 //R2上的默认路由
-
查看Tunnel状态,以及PC1和PC2之间的连通性。ipsec policy name: p1ipsec policy sequence: 100negotiation mode: manualsecurity acl: 3000local address: 192.168.13.1remote address: 192.168.23.2proposal name: trans1esp(inbound) setting:esp spi: 654321 (0x9fbf1)esp string-key: fdsaesp encryption-hex:esp authen-hex:esp(outbound) setting:esp spi: 123456 (0x1e240)esp string-key: asdfesp encryption-hex:esp authen-hex:OutBound SA has been established.InBound SA has been established.//路由器R1端的Tunnel状态ipsec policy name: p2ipsec policy sequence: 200negotiation mode: manualsecurity acl: 3001local address: 192.168.23.2remote address: 192.168.13.1proposal name: trans2esp(inbound) setting:esp spi: 123456 (0x1e240)esp string-key: asdfesp encryption-hex:esp authen-hex:esp(outbound) setting:esp spi: 654321 (0x9fbf1)esp string-key: fdsaesp encryption-hex:esp authen-hex:OutBound SA has been established.InBound SA has been established.//路由器R2端的Tunnel状态//在PC1上pingPC2正在 Ping 192.168.200.2 具有 32 字节的数据:来自 192.168.200.2 的回复: 字节=32 时间=3ms TTL=254来自 192.168.200.2 的回复: 字节=32 时间=9ms TTL=254来自 192.168.200.2 的回复: 字节=32 时间=3ms TTL=254来自 192.168.200.2 的回复: 字节=32 时间=3ms TTL=254来自 192.168.200.2 的回复: 字节=32 时间=9ms TTL=254
- 配置自动方式的Tunnel。
[R1]ipsec policy p3 300 isakmp[R1-ipsec-policy-p3-300]security acl 3000[R1-ipsec-policy-p3-300]proposal trans1[R1-ipsec-policy-p3-300]tunnel local 192.168.13.1[R1-ipsec-policy-p3-300]tunnel remote 192.168.23.2[R1-ipsec-policy-p3-300]quit[R1]ike pre-shared-key 12345 remote 192.168.23.2[R1]interface e0/0[R1-Ethernet0/0]ipsec policy p3//提议和手工方式一样,策略修改为自动方式的,而且共享密钥的设置,Tunnel两端要一致。[R2]ipsec policy p4 400 isakmp[R2-ipsec-policy-p4-400]security acl 3001[R2-ipsec-policy-p4-400]proposal trans2[R2-ipsec-policy-p4-400]tunnel local 192.168.23.2[R2-ipsec-policy-p4-400]tunnel remote 192.168.13.1[R2-ipsec-policy-p4-400]quit[R2]ike pre-shared-key 12345 remote 192.168.13.1[R2]interface e0/0[R2-Ethernet0/0]ipsec policy p4
-
Tunnel状态以及PC1和PC2之间的连通性。ipsec policy name: p3ipsec policy sequence: 300negotiation mode: isakmpsecurity acl: 3000remote address 0: 192.168.23.2Proposal name: trans1ipsec sa duration: 3600 secondsipsec sa duration: 1843200 kilobytesOutBound SA has been established.InBound SA has been established.//路由器R1端的Tunnel状态ipsec policy name: p4ipsec policy sequence: 400negotiation mode: isakmpsecurity acl: 3001remote address 0:192.168.13.1Proposal name: trans2ipsec sa duration: 3600 secondsipsec sa duration: 1843200 kilobytesOutBound SA has been established.InBound SA has been established.//路由器R2端的Tunnel状态正在 Ping 192.168.200.2 具有 32 字节的数据:来自 192.168.200.2 的回复: 字节=32 时间=3ms TTL=254来自 192.168.200.2 的回复: 字节=32 时间=9ms TTL=254来自 192.168.200.2 的回复: 字节=32 时间=3ms TTL=254来自 192.168.200.2 的回复: 字节=32 时间=3ms TTL=254//从PC1 ping PC2的情况
H3C-×××的配置
拓扑图
上一篇: A Crash Course in 3D
下一篇: spring security3 dem
- openvpn linux客户端使用
51284
- H3C基本命令大全
50736
- openvpn windows客户端使用
41334
- H3C IRF原理及 配置
38144
- Python exit()函数
32612
- openvpn mac客户端使用
29514
- python全系列官方中文文档
28364
- python 获取网卡实时流量
23233
- 1.常用turtle功能函数
23201
- python 获取Linux和Windows硬件信息
21526
- Python搭建一个RAG系统(分片/检索/召回/重排序/生成)
1597°
- Browser-use:智能浏览器自动化(Web-Agent)
2330°
- 使用 LangChain 实现本地 Agent
1932°
- 使用 LangChain 构建本地 RAG 应用
1873°
- 使用LLaMA-Factory微调大模型的function calling能力
2201°
- 复现一个简单Agent系统
1914°
- LLaMA Factory-Lora微调实现声控语音多轮问答对话-1
2601°
- LLaMA Factory微调后的模型合并导出和部署-4
4370°
- LLaMA Factory微调模型的各种参数怎么设置-3
4216°
- LLaMA Factory构建高质量数据集-2
2993°
- 姓名:Run
- 职业:谜
- 邮箱:383697894@qq.com
- 定位:上海 · 松江